Time for a re-brand: Cloud Renegade
TL;DR – I’m moving my blog to https://www.cloudrenegade.us
Well, lots of things are changing for me. You’ll get to hear more about that next week but for now, I’m going away from phyler.wordpress.com to a whole new brand. This site was started in the aftermath of my home server dying back in 2006. I had been blogging from ~2002ish? to 2006 on a server in my basement. It was a fun way to learn about blogging. It eventually died and I moved here. I never bothered to get a custom domain assigned, mainly due to cost.
Recently, while thinking on branding, the name Cloud Renegade came up and I really liked it. Enough that I decided to be like a few of the other folks (looking at you Michael LaMontagne) and explore the world of Static Site Generators and hosting my blog on my Azure subscription. I’ll do a post on that adventure soon.
So, what does this all mean? It means that I’m moving my blog to https://www.cloudrenegade.us. You will need to update your favorite RSS Reader with https://www.cloudrenegade.us/index.xml.
Microsoft Teams and Call-me Back Changes
Was tipped off to this from a friend. For a long time, we’ve had the Call-me back feature as part of Teams. Microsoft has stated it would change several times over the past year or so, but it looks like it is finally going to happen:
Customers have been provided a complimentary dial-out capability that will end on November 30, 2019. Beginning December 1, 2019, each Audio Conferencing subscription provides 60 minutes per user per month that can be used to dial out to non-premium numbers in ANY of the Zone A countries as described in this document. Your tenant dial-out minute pool size is based on assigned licenses and not purchased licenses. This benefit is applicable to Audio Conferencing monthly subscription licenses and does not extend to Audio Conferencing pay-per-minute licenses.
You can find out all the details at: https://docs.microsoft.com/en-us/microsoftteams/audio-conferencing-subscription-dial-out
Since the change will go into effect on December 1st, 2019, now is the time to start watching your pool minutes. To do this, you need to sign in to the Legacy Portal (Skype for Business Online vs the Modern Portal).
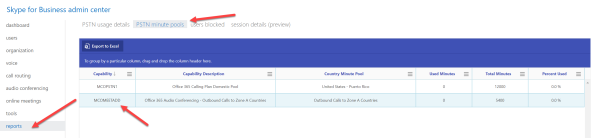
Then go to Reports, then PSTN Minute Pools and you should see something like this (I took this snap from a test tenant that I don’t use for PSTN/Conf hence, nothing used, yours should look different if people are using the Call-me back feature):
From the article:
Email notifications will be sent to all tenant administrators of a given customer when the utilization of the tenant’s dial-out minutes pool has reached 80% and 100%.
This is one of those areas where IT Pro’s need to stay vigilant on what changes are happening and then working with the proper groups to ensure that end users know to try and use Teams with VoIP whenever possible (besides, it’s a better experience than a PSTN call when you have proper bandwidth). I have actually found that the Teams mobile app does a great job keeping my VoIP call going even when switching from wireless to LTE to wireless and back to LTE.
There is a lot of great information in this article such as how to calculate the minutes you get and which countries are included.
If you’ve read this far, you’re probably asking yourself, what happens if I run out? Glad you asked, you get to buy Communications Credits. You need to have this setup and the meeting organizer must also be enabled to use them. If not, the outbound call won’t happen.
The other question you may be asking yourself (I know I am) is “what happens if the minute pool is exceeded mid-call and I don’t have Communications Credits configured?” To that, I don’t know. My guess is that the call will continue and the next call-me back attempt will fail if Communications Credits are not setup. That said, it’s just a guess at this point and given that we are still months away from the change, anything that is stated today, could very well change by December 1st. I will add, if you aren’t willing to setup Communications Credits, you probably should just turn off the Call-me back feature. I know I wouldn’t want to have a user call in to the Help Desk to get an answer of “Well, we ran out of minutes and won’t pay for more, that’s why the feature you’ve used all month is now broken”. That’s ultimately a poor user experience. Better than to do without completely in that case.
CapitalOne, AWS and what we should learn (or really know) about Public Cloud
I’m sure you’ve heard all about the CaptialOne hack by now. The interesting part is that the records were stored on AWS. You can read more about that here. Why is this interesting? Number one reason is that AWS wasn’t the issue but the hack has highlighted the fact that while AWS and other public Cloud providers (i.e. Microsoft and Google) provide the infrastructure, you still need to be responsible about the applications. No different than when you run on-premises, you are still responsible for the configuration of the applications and devices.
If you are using Office 365 for example, you should utilize Secure Score as a starting point. Secure Score can help you identify areas which are not following to best practices (i.e. do you have Global Admin’s without MFA?)
I spend a lot of time with customers talking about these types of topics. I hear many people say if they move to the Cloud they won’t have a job. This is all bogus unless your job is literally just racking and stacking hardware in a data center, in which case, you may not have a job at your current company but possibly at the Cloud provider. When a company moves to the Cloud, if you are responsible for an application, your job hasn’t changed, just the location of the server has changed. In fact, your job became more important. It is your responsibility to ensure that the application is setup to best practices and to ensure that it is meeting business needs.
Take the time to learn and embrace the Cloud. There are many opportunities that didn’t exist before with Public Cloud. I personally believe that Public Cloud and the consumerization of technology is benefiting businesses through improved productivity. Companies have to get real value out of applications or they will (and can) drop them quickly in favor of alternatives that perform. Embrace the new challenges and discover that the world hasn’t really changed all that much.
Microsoft Teams Adoption and the Impact of Emotions
Lately, I’ve found myself studying the science of Adoption and Change Management (ACM). Mainly because Microsoft Teams is a pretty big foundational shift from how we’ve done things in the OCS/Lync/Skype world in some ways. In other ways, we’re faced with the same ACM struggles as OCS/Lync/Skype of simply getting the users to understand the software and how it can improve their lives.
I had two things happen to me today that compelled me to write this article. In both cases, the events brought up and out emotions from me (even if I do joke that my emotions like my taste buds are dead, yes, I like spicy food, but I digress).
The first was a call where I was discussing Microsoft Teams vs Slack. The person wanted to know how I could convince a group of Slack users to migrate to Microsoft Teams. They thought I could just drop some tech specs and be done with it. I had to be frank with them, in my experience, Slack users are a very passionate bunch. They enjoy the product and feel it improves their lives. Based on this passion, there is a raw emotional tie to it. At this point, rational thought of tech specs flies out the window. I then explained, it’s no different really than my passion for Microsoft and its solution. I am deeply passionate around the tech that Microsoft creates. I become emotional speaking about it (ask my co-workers who brace themselves when my soapbox comes out). The emotion it invokes is ultimately, irrational, no different than my friends who are passionate for Slack.
The second event was an email. Yes, a simple email. It contained information that I really didn’t want to read. It was negative and I knew it. It created that emotion in me to want to walk away. Here I am, a person who has to have crucial conversations regularly with folks and a simple email had me spun up. Similar to those times when younger one might breakup with a boyfriend or girlfriend and just not want to speak to that person ever again, then promptly see them the next day.
As I pondered over these two events, I realized that they both point to the same thing, we as humans, do things irrationally a lot of the time based on our emotions. No matter how much we think we are logical, as soon as our emotions are involved, we can easily make choices from those emotions instead of logic. Don’t get me wrong, these emotions are not bad nor is the fact that we act based on them. In fact, a good amount of our survival is tied to them.
So, how does this actually tie back to the original point? It’s simple, I’m not going to be able to just drop logic and convince them to change. As change agents, we need to surround people with information and appeal to their emotional side in order to get them to change. It’s what we subject ourselves to every day when we turn on the TV, watch videos on YouTube, or simply go to our favorite news site. We see the ads that try to convince us that we need those products to be able to be better individuals, have nicer things, whatever.
As you approach your project, whether it is Microsoft Teams or any other product, are you thinking about how you will appeal to your targeted users’ emotional connection to it?
Resource Accounts in Microsoft Teams and how they affect Auto Attendants and Call Queues (new, maybe?)
UPDATE 7/24/2019: The new license model has been released. Please reference https://docs.microsoft.com/en-us/microsoftteams/teams-add-on-licensing/virtual-user for guidance.
This might be one of those classic “Adam” moments. Maybe this has been this way and I’m only waking up to it now. That said, I have found in life, that if I have a question or a view, I’m usually not the only one who has it. So here goes.
Had someone bring this link up to me recently (HT to Randy, he’ll know who he is): https://docs.microsoft.com/en-us/microsoftteams/manage-resource-accounts
This link is all about Managing Resource Accounts in Microsoft Teams. No big deal right? We use Resource Accounts regularly for things like Rooms in Exchange, etc. In Skype for Business (On-prem or Online) or Teams, we create Resource Accounts for Room accounts as well. Guess what else needs a Resource Account now? Your Auto Attendants and Call Queues!
In the past, if you had purchased Phone System licenses, you were able to request and assign a certain number of Service Numbers within your tenant. Those could be assigned to Auto Attendants and Call Queues. This has changed (or is changing) to require each Auto Attendant or Call Queue to have a Resource Account created for them and then the kicker, if you want a phone number assigned, you have to assign an E1, E3, or E5, with the Phone System license and use either Direct Routing or assign a Calling Plan!
If you don’t need to assign a phone number, you simply need to create the Resource Account. You do not need to license the Auto Attendant or Call Queue if they will not have a phone number.
For some people this is not a big deal. If you have lots of Auto Attendants or Call Queues that have phone numbers assigned, this could have an impact on the Microsoft licensing that you need going forward.
It’s important to properly plan your deployment and this is a perfect example. Since we can nest Auto Attendants and Call Queues, not every one of them needs a phone number. Utilize this whenever possible.
The ultimate reason for this, I would guess, is that this is how an Auto Attendant or Call Queue will be enabled to dial out (i.e. when you want your afterhours Help Desk to forward to someone’s mobile device).
I really feel like I should have seen/known about this one but I’ll be honest, it snuck up on me. My MVP friends will all be like “don’t you remember hearing about this?” or something and give me a hard time, but it’s public now and hopefully, if you’ve read this far, you’ve found it useful information.
Speaking at ConvergeOne 2019 Iowa Tech Summit
I’ll be speaking at the ConvergeOne 2019 Iowa Tech Summit in Des Moines on April 17th. I’m going to be talking on Microsoft Teams and it’s impact on Digital Transformation. Here’s a quick snippet on the topic:
Microsoft Teams is impacting the way companies work. From the mindset of Cloud First, Mobile First, Microsoft has established Teams as the hub for Collaboration. In this presentation, we will look at five ways that Teams is enabling Digital Transformation and give some thoughts on how it could impact your organization.
If you are in the area and would like to come join, you can register here.
Microsoft Teams Tip Tuesday – Give more context!
This tip is somewhat based on last week’s tip. When posting a conversation into a Microsoft Teams channel, give as much context as possible. If you are posting a link, tell what the link is about, don’t just post the link. Also, tag people if you want them to see it specifically. Many times, we post things in a Channel and it ultimately just becomes a large “junk” drawer of content. There is a lot of valuable information in the channel but we can’t find it easily. By giving context and tagging people, it becomes easier to search for the information.
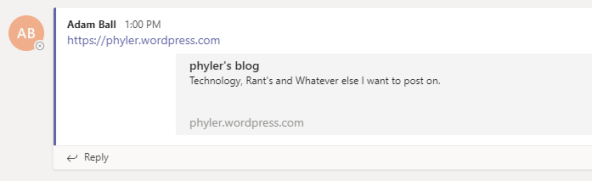
Here’s a quick example. In the first image, I’ve posted a link to the channel but given no context.
Teams has gone ahead and given us a quick preview of the site but that’s it. We have no idea why this link is here. The same could apply to a file dropped into the channel as well.
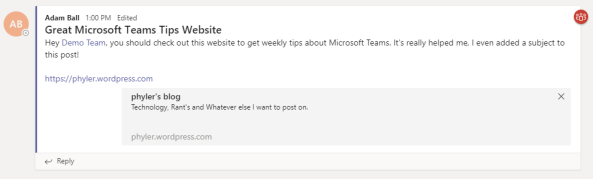
Here’s a second example where I’ve given more context to the post:
You can see that I added a subject and I tagged the Demo Team and told them why they should pay attention to this awesome website.
By doing these things, when new members get added to the Team, they can search for content and be able to better discover Microsoft Teams Tips now.
Microsoft Teams Tip Tuesday – Add a Subject to a Conversation
This is one that has become pretty common to many of the Teams that I am a part of and I have seen it documented by a few others but felt like it needs more publicizing.
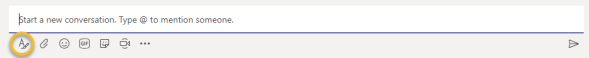
If you are starting a new conversation, add a subject to make it more engaging. This really helps if you have multiple conversations going on in a Channel. This is super easy to do. Right below the “Start a new converstation” where you would type, there is an icon that has an “A” with a pencil on it:
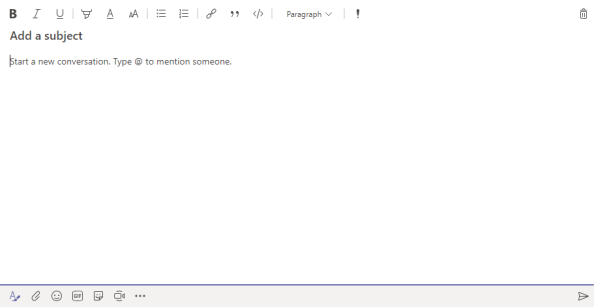
Now you will be presented with the ability to edit the subject field:
Bonus tip: Another thing about this mode, you can free form enter text and even craft paragraphs. When you hit the “Enter” key, you will get a new paragraph versus posting the text to the Channel.
Hoping to bring more of these types of tips in the coming weeks!
Meetings location in Microsoft Teams
I’m sure some of my blog readers remember back when OCS or Lync came out we’d get a brand new CHM file that we would comb over looking for what was new or changed. Everything at the time had that new tech smell. It was awesome. I’ll be honest, learning something new about a technology never gets old for me. This blog post is a perfect example of why. I was doing a walk-through of a presentation I was going to help with and the speaker had a slide in there that caught my eye. I literally said “wait, stop, go back to the previous slide!”. As I read it, my eyes were opened to something I didn’t know and it took me back to those days of reading the CHM for something new.
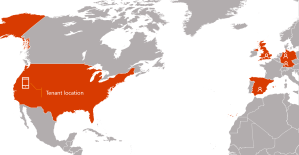
What caught my eye was this: A Microsoft Teams conference is hosted by Office 365 cloud in the same region where the first participant joined. Why is that such a big revelation? Cause in the on-premises world, that would never happen. In the on-prem world, we always knew that the MCU was based on the meeting organizer.
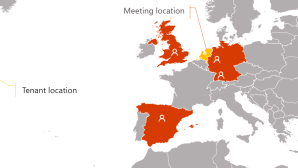
Why is this so fascinating to me? Well, think about it from a global perspective. If I have 10 folks invited to a meeting and let’s say that some are in the US and Some are in Europe. If a person in Europe is the first person to join, then the MCU will be in Europe.
Here’s a quick example:
This thought is why it is really important to plan your approach to Microsoft Teams appropriately. If you have centralized Internet or something that could delay a user getting on to the Microsoft network quickly, then it could have an impact on meeting quality. You can take a look here for the thoughts around preparing your network for Microsoft Teams: https://docs.microsoft.com/en-us/microsoftteams/prepare-network.
Something to note here, we are talking about the data in flight portion of the meeting only. The MCU is where all the media streams go to and get redistributed to the participants. We are not talking about the data at rest (i.e. meeting notes, attachments, etc.). That is all still kept safe and secure based on the meeting organizer’s location and tenant. This is important as we don’t want to cross security or governance boundaries.
If you want more info around the Meeting location, you can find the documentation to it here: https://docs.microsoft.com/en-us/microsoftteams/microsoft-teams-online-call-flows#principles. (HT to Bryan Nice for helping me find the specific link). Always stay learning my friends!
Comms vNext Thanks!
By the time you read this, it will be Monday morning. I wanted to take just a moment to thank everyone who made Comms vNext 2018 possible.
First and foremost, I want to thank the community and everyone who showed up. Without the community and folks desiring an event like this, we would never have attempted it.
Second, I want to thank the speakers and the volunteers who worked tirelessly to make the day so special. In no particular order:
- Jamie Stark
- Doug Lawty
- Jens Madsen
- Alan Shen
- Heidi Gloudemans
- Kevin Peters
- Brian Ricks
- Anthony Caragol
- Nick Smith
- Laurie Pottmeyer
- Allen Wat
I also want to thank Allison and Darphene at Microsoft who run the Denver office. They were amazing and so helpful for making sure we had what we needed for the event space.
Next, our sponsors. These folks stepped up to the plate and believed in what we were doing and helped bring the event to life. Many of them flew in straight from another conference and just kept going even though they were tired and worn-out. We never knew it because they brought a ton of energy and knowledge to the day.
Last and not least, my co-organizers. Josh, Pat, Jonathan, you guys were amazing. Everyone contributed and the creativity that flowed from all of you was fantastic. I believe all four of us were needed to pull this off. The way everyone helped and put forth ideas and made sure things got done while we all did our day jobs just showed what can be done as a Team.
Speaking of Teams, this entire event was planned via Microsoft Teams. Yes, you read that right. We met and discussed the event in Teams. There were probably 50+ iterations of the logo and shirts posted in threads. Teams made this event possible.
I thought the event was amazing. I hope if you attended, you do too. If you didn’t or couldn’t attend, please stay involved in the community and make sure your desire to see an event like this happen again is heard. We are listening and so is Microsoft.
If I forgot someone, please pardon me. So many people contributed. There was lots of advice given to us in the background and if I had to name everyone, it would be an endless list.
Thank you.